Students from Taiwan Tech have achieved remarkable success in developing a malicious software detector and an intelligent contract vulnerability scanning system.
In the 28th International ICT Innovative Service Awards, organized by the Ministry of Digital Affairs, the Ministry of Education, and the CSIM of the Republic of China, students from the Department of Computer Science and Information Engineering at the Taiwan Tech won the first and second place in the Cybersecurity Innovation Application Group with their projects “Machine Learning-Driven Robustness Assessment Platform for Malicious Software Detectors” and “Contract Guardian - Intelligent Contract Vulnerability Scanning and Analysis”. The supervising professor, Shao-Jui Wang, emphasized that the department stresses the importance of balancing theory with practical application, requiring students to possess innovative thinking aligned with industry demands, enabling them to become information engineering leaders with innovative capabilities.
The International ICT Innovative Service Competition is Taiwan's largest ICT application competition, with intense competition this year, drawing a record high of 102 schools, 1,382 teams, and 7,059 participants. The project “Machine Learning-Driven Robustness Assessment Platform for Malicious Software Detectors”, securing first place in the Cybersecurity Innovation Application Group, was jointly developed by students from the Department of Computer Science and Information Engineering, including Yan-He Chen, Wei-Ren Liao, Chia-Chun Shih, Hsiang-Ying Tsai, Yi-Chun Cheng, and Chao-Chun Chang. Yan-He Chen, currently a second-year master's student in the Department of Computer Science and Information Engineering and the team leader, explained that the malicious software detection platform provides an open environment for users to upload detectors and select various adversarial attack samples for testing, enabling users to understand the strengths and weaknesses of the detectors and make improvements.

The “Machine Learning-Driven Robustness Assessment Platform for Malicious Software Detectors” secured first place in the Cybersecurity Innovation Application Group. From the front row, left to right: Chao-Chun Chang, Yan-He Chen, Yi-Chun Cheng, Chia-Chun Shih, Hsiang-Ying Tsai, Wei-Ren Liao.
Yan-He Chen smiled and mentioned that everyone in the team participated in the competition with a relaxed attitude, never expecting to win. After the second-place announcement, everyone was already packing up to leave. However, the unexpected win filled them with both surprise and emotion. Despite winning first place in this competition, Yan-He Chen humbly suggested that the malicious software detection platform could further expand by adding more upload specifications, broadening its application scope, reducing user limitations, and enhancing convenience. He also expressed gratitude to all team members for their efforts that led to this sweet success.
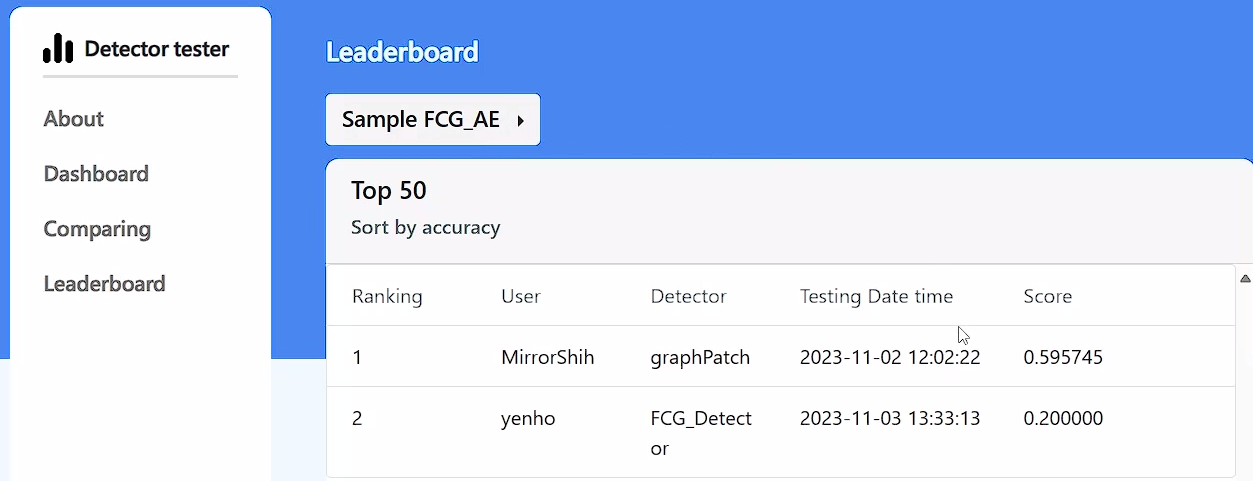
The “Robustness Assessment Platform for Malicious Software Detectors” allows users to observe the performance of other detectors and rank them, aiding users in understanding the strengths and weaknesses of detectors for further improvements.
In recent years, blockchain technology has thrived. To prevent hackers from modifying smart contract vulnerabilities in transactions involving cryptocurrencies and NFTs, Bo-Jun Wang, Pin-Jing Lai, and Xin-Yi Wang decided to develop an “Intelligent Contract Vulnerability Scanning and Analysis” system. Team leader Bo-Jun Wang explained that a smart contract is a special protocol used in blockchain. Once deployed by the developer, a smart contract operates entirely on the blockchain, processing transactions. Therefore, once the conditions specified in the protocol are met, the transaction is automatically executed.

The “Contract Guardian - Intelligent Contract Vulnerability Scanning and Analysis” won second place in the Cybersecurity Innovation Application Group. From the front row, left to right: Xin-Yi Wang, Pin-Jing Lai, Bo-Jun Wang.
However, smart contracts can also be vulnerable to hackers who may exploit programming flaws to steal user assets. Hence, it becomes crucial to detect these vulnerabilities through a system to prevent potential exploitation. Bo-Jun Wang mentioned that the current system supports only two platforms, Ethereum and EOSIO, and they hope to expand it to include Cardano or other contract platforms in the future. Additionally, they have developed an AI system to assist in detecting contract vulnerabilities, aiming to enhance the system's security further.
Witnessing multiple awards received by students from the Department of Computer Science and Information Engineering, faculty members, including Professor Shao-Jui Wang, expressed great joy. He pointed out, “The department not only emphasizes coding but also stresses the ability to propose and create new technologies from existing ones”. With this, he hopes that students in the department can possess innovative thinking and become leaders who lead their teams forward.
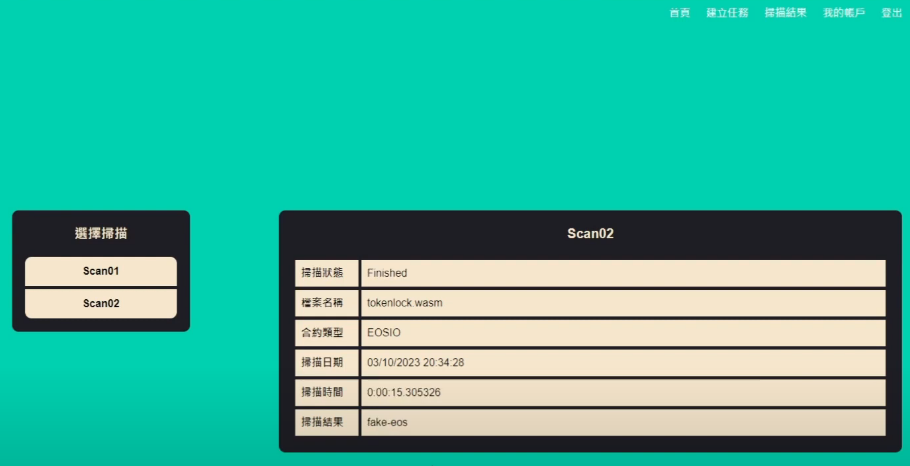
After scanning with the “Intelligent Contract Vulnerability Scanning and Analysis” system, a vulnerability named “fake-eos” was discovered in this smart contract.